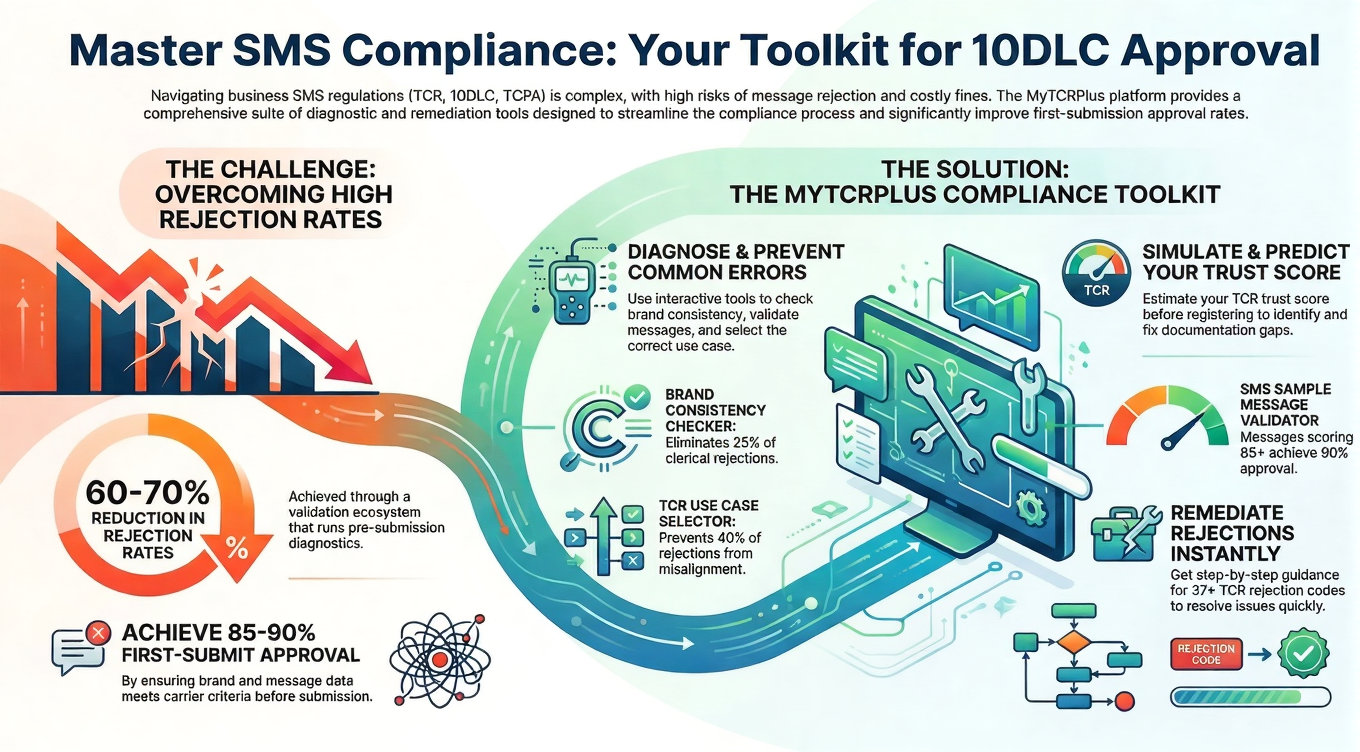
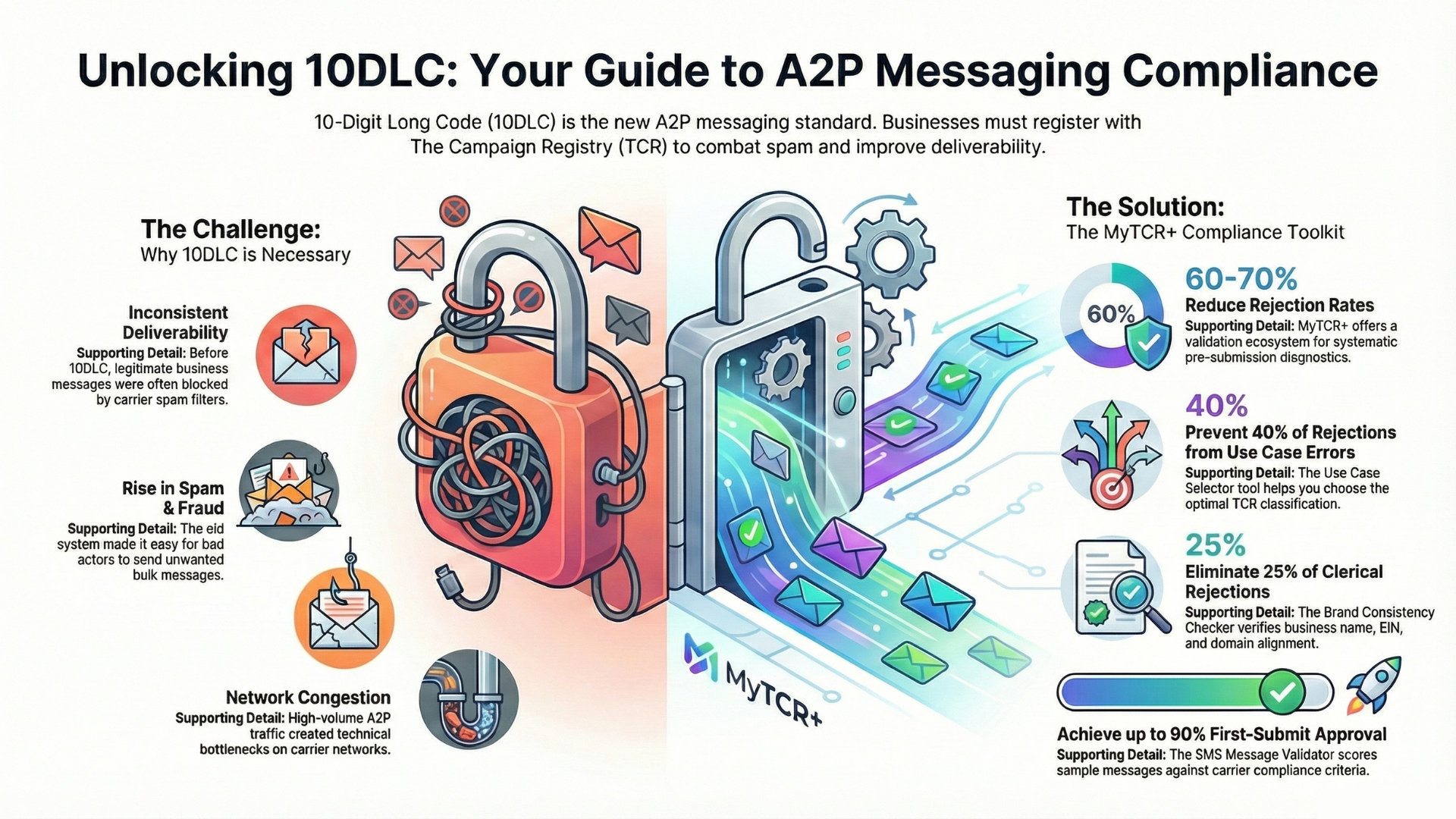
The telecommunications landscape is undergoing a significant transformation as major carriers implement increasingly stringent policies to combat spam, fraud, and abuse on their networks. What began as occasional enforcement actions has evolved into a comprehensive regulatory framework that fundamentally affects how businesses communicate with customers through voice and messaging channels. Understanding this evolution isn’t optional for companies that rely on direct customer communication—it’s increasingly essential for operational survival in a digital-first business environment.
The Catalyst for Change: Understanding the Problem Behind Carrier Crackdowns
To understand why carriers are tightening their policies so dramatically, it’s important to recognize the severity of the problem they’re addressing. Mobile network operators have faced mounting pressure from regulators, government agencies, and consumers alike to address the surge in unwanted communications flooding their networks. What was once a minor annoyance has escalated into a crisis that undermines the fundamental utility of mobile communications.
Statistics tell a compelling story. Americans receive billions of robocalls and spam text messages annually, with some estimates suggesting the average person receives at least a dozen unwanted calls per month. These communications represent more than mere nuisances—they pose genuine security threats that erode consumer trust in mobile communications, create opportunities for fraud and identity theft, and damage the brand reputation of carriers themselves as consumers blame the networks for failing to protect them.
Regulators have taken notice. The Federal Communications Commission (FCC), Federal Trade Commission (FTC), and state attorneys general across the country have launched investigations, held hearings, and issued enforcement actions against both the perpetrators of spam and the carriers perceived as inadequately protecting consumers. Congress has become involved, with multiple pieces of legislation proposed to strengthen protections and impose stricter obligations on carriers. This regulatory pressure has transformed carrier anti-spam efforts from a nice-to-have into a regulatory imperative.
Consumer frustration has similarly intensified. As spam messages and robocalls proliferate, people have grown less trusting of their mobile devices—the very communications channels businesses depend on to reach them. This erosion of trust creates a vicious cycle: legitimate messages get lost in filters and significant calls get blocked, making customers more skeptical of mobile communications. This skepticism further encourages defensive filtering, complicating the challenge for businesses trying to reach their customers.
In response to this multifaceted pressure, carriers have shifted fundamentally from reactive to proactive enforcement strategies. Rather than responding to complaints after problems occur, carriers now actively police their networks in real-time, implementing sophisticated systems designed to prevent abuse before it reaches consumers.
The Technology Revolution: How Carriers Identify and Block Suspicious Activity
The enforcement mechanisms carriers now employ would have seemed like science fiction just a few years ago. Modern telecommunications carriers utilize sophisticated analytics and machine learning algorithms to identify suspicious patterns in real-time, analyzing communications as they traverse the network and making immediate decisions about whether to allow, slow, or block transmissions.
These systems evaluate an astonishing array of factors to assess the legitimacy of communications. They examine message velocity—how quickly messages are sent from a particular number or account, flagging unusual spikes in volume that might indicate spam campaigns. They analyze content patterns, looking for repetitive language, suspicious keywords, or formatting characteristics associated with known spam. Additionally, they evaluate sender reputation based on historical performance, recipient engagement metrics, complaint rates, and other signals accumulated over time.
The sophistication of these algorithms continues to increase as carriers invest heavily in artificial intelligence (AI) and machine learning capabilities. Systems that once operated with relatively simple rules now employ complex neural networks capable of detecting subtle patterns that humans might miss. A carrier’s filtering system might analyze the relationship between message content, sending time, recipient location, sender history, and numerous other variables simultaneously to assign a spam probability score to each individual message.
What makes this technology particularly challenging for legitimate businesses is its opacity. Carriers do not publicly disclose exactly how their algorithms work, what specific factors trigger filtering or blocking, or how scores are calculated. This creates a scenario where a business could be sending communications they believe are completely legitimate, only to discover that a significant percentage of those messages never reach their intended recipients. Without clear feedback about what triggered the filtering, businesses are often left guessing at the cause and struggling to remediate the problem.
The speed of these systems is also remarkable and problematic. Where old enforcement mechanisms might have involved human review and warnings, modern systems make filtering decisions instantaneously as messages enter the network. By the time a business realizes messages are being blocked, thousands may have already been filtered or rejected. This real-time enforcement leaves little room for human judgment or appeals.
Registration Requirements: The New Gatekeeping Framework
Registration requirements represent perhaps the most visible and consequential change in this new carrier landscape. Previously, businesses could send messages with minimal oversight—simply acquiring a phone number or short code and beginning to transmit. Now, they must navigate complex registration processes that verify their identity, use cases, and operational practices.
The 10DLC (10-Digit Long Code) framework represents a significant evolution in registration requirements for business messaging. Instead of allowing any company to simply begin using standard phone numbers for bulk messaging, carriers now require companies to register their brands and specific campaigns. This registration process involves providing detailed information about the business, its industry, the types of messages being sent, the intended recipients, and the specific use cases for communications.
After registration, carriers assign trust scores to each registered entity and campaign. These scores determine throughput limits—how many messages a particular sender can transmit per second or per day—and influence deliverability. A business with a high trust score enjoys generous throughput limits and prioritized delivery, while one with a lower score might face significant restrictions. This creates a hierarchy of legitimacy, where established businesses with strong reputations enjoy better access than smaller companies or those without extensive track records.
The registration paradigm has created both benefits and barriers. While it has made it more difficult for outright fraudsters to operate at scale—deterring the most casual bad actors—it has also created new barriers to entry for legitimate businesses, especially smaller companies or startups without extensive operational histories. The registration process requires time, effort, and sometimes external expertise to navigate successfully. Different carriers maintain different registration requirements and processes, forcing companies to learn multiple systems. Getting rejected or delayed in the registration process can severely impact business operations.
Furthermore, the registration system has also created new opportunities for legitimate businesses to be incorrectly flagged or blocked. A company might register in good faith but still find itself subjected to restrictions if the carrier suspects any policy violation. The burden of proof and the ability to appeal adverse decisions are often unclear, leaving companies uncertain about their rights and remedies.
Content Filtering: When Legitimate Messages Get Trapped in the Net
Content filtering has become increasingly aggressive across all major carriers, creating significant challenges for businesses attempting to send legitimate communications. Messages containing certain keywords, shortened URLs, formatted messages that resemble known spam patterns, or other characteristics associated with fraudulent communications face automatic filtering or blocking.
The challenge lies in understanding what triggers filters. A promotional message about a financial service might be flagged due to keywords historically associated with fraud scams. An order confirmation might be blocked because it contains a shortened URL that the filtering system doesn’t recognize. A two-factor authentication code could be delayed because the message formatting resembles phishing attempts.
Even businesses that believe they are sending completely legitimate communications find them trapped in invisible filters, often unaware that their messages are not reaching intended recipients until customers start complaining about missing notifications or receipts.
The opacity of these filtering systems creates significant operational challenges. Carriers seldom provide detailed feedback about why specific messages were blocked or filtered. A business might receive a simple report indicating that “3,000 messages failed to deliver” without an explanation of which messages failed, to which recipients, or for what reason. Without this intelligence, businesses struggle to identify and remediate problems.
This lack of transparency has led many businesses to adopt overly cautious content policies, removing potentially useful information from messages to minimize the risk of triggering filters. This defensive approach can reduce message quality and effectiveness, yet many companies feel it is necessary to ensure message delivery. Thus, carrier policies, even when intended to protect consumers, can degrade the quality of legitimate business communications.
Penalties for Violations: Escalating Stakes and Permanent Consequences
Penalties for policy violations have escalated dramatically in the modern carrier enforcement environment. Enforcement mechanisms have shifted from warnings and temporary suspensions to permanent, severe consequences that can terminate a business’s ability to communicate with customers.
Where former carrier policies involved warning letters and brief suspensions, modern enforcement is far more punitive—permanent bans now prevent a business from using their network for communications. Such bans are often non-negotiable and non-appealable; once implemented, they are effectively permanent.
Beyond individual carrier bans, violating carriers share blacklists, creating situations where a company banned by one major carrier may find itself banned by multiple carriers simultaneously. This domino effect means that a single violation can shut down a company’s ability to reach customers across all networks. For businesses that rely on voice calls or text messages for critical functions, such as two-factor authentication or order notifications, this represents an existential threat.
Financial penalties have also increased substantially, with carriers assessing steep monetary fines for violations. In some cases, carriers even pursue legal action to recover damages from companies believed to have engaged in systematic abuse. These costs extend beyond penalties to include legal fees, remediation efforts, reputation damage, and lost revenue from customers who cannot be reached during enforcement actions.
Importantly, these penalties are often applied with minimal due process. A business might suddenly find its communications blocked, its numbers suspended, and its traffic cut with little warning or opportunity to respond. By the time a company understands what has happened and attempts to rectify the situation, it may already have suffered substantial damage.
Voice Communications: STIR/SHAKEN and the Authentication Revolution
The evolution of carrier policies extends beyond text messaging into voice communications, where similar tightening measures are underway. The implementation of STIR/SHAKEN protocols represents a fundamental shift in how caller identity is verified and authenticated in voice networks.
STIR/SHAKEN stands for Secure Telephone Identity Revision (STIR) and Signature-based Handling of Asserted information using toKens (SHAKEN). These protocols authenticate caller identity and make it much harder for bad actors to spoof phone numbers—a common tactic used in robocall fraud schemes. When a call arrives from an authenticated number, it displays to the recipient as verified and legitimate, helping consumers distinguish between legitimate business calls and fraudulent ones.
However, the implementation of STIR/SHAKEN has also created unintended consequences for legitimate businesses. Companies using shared telecommunications infrastructure or complex call routing systems sometimes find their calls incorrectly labeled as “Scam Likely” or blocked entirely, despite having properly authenticated call credentials. A business making legitimate customer service calls might find many calls rejected before reaching the recipient’s phone.
These authentication challenges create friction in customer relationships and can undermine service quality. Customers may miss important calls from legitimate businesses because their phones automatically reject them due to incorrect STIR/SHAKEN assessments. This can result in higher call abandonment rates and more inquiries from customers trying to reach the business through alternate means.
Remedying these authentication issues can be complex and time-consuming. Businesses must work closely with telecommunications providers to ensure proper authentication, may need to implement additional verification measures, and frequently invest in expertise to navigate the technical requirements.
The Compliance Challenge: Navigating a Complex Multi-Carrier Environment
The evolution of carrier policies has created a fundamentally more complex compliance environment for businesses. Organizations must navigate carrier-specific requirements, each with subtle differences and varying enforcement approaches.
Different carriers have different registration requirements, content filtering policies, throughput limits, and enforcement mechanisms. A message that passes filtering on one carrier may be blocked by another. A registration that satisfies one carrier’s requirements may be insufficient for another. Businesses must invest significant resources in understanding each carrier’s specific requirements and maintaining compliance with each.
This complexity is particularly challenging for smaller businesses and startups that lack dedicated compliance teams. Large enterprises with telecommunications expertise can afford specialists to navigate carrier policies, but smaller companies often lack the resources to remain current with rapidly changing requirements, creating an unequal playing field.
Additionally, carrier policies continue evolving as carriers refine their enforcement mechanisms, update their algorithms, and respond to new types of abuse. What was compliant six months ago might violate policies today. Businesses must continuously monitor for policy changes, update practices accordingly, and invest in ongoing compliance education and training.
Best Practices for Operating in the Modern Carrier Environment
Successfully navigating the contemporary carrier landscape requires a multi-faceted approach that combines technical implementation, operational discipline, and ongoing monitoring and adaptation.
Conduct a Comprehensive Audit: Businesses should begin by auditing their current communications practices. This includes reviewing registration status with all carriers, analyzing message content for compliance issues, assessing sender reputation metrics, and identifying practices that might trigger filtering or violations.
Invest in Proper Registration: Ensure accurate and detailed registration with all carriers used for business communications. Provide clear descriptions of the business, its industry, use cases for communications, and recipient preferences. Maintain records of registration information and update them promptly if practices change.
Implement Robust Consent Management Systems: Maintain clear records of customer opt-in to demonstrate compliance when questions arise. Make opt-out mechanisms easy to use, and promptly honor all unsubscribe requests.
Develop Communication Best Practices: Minimize the risk of triggering content filters by using full URLs instead of shortened ones, avoiding excessive capitalization or special characters, varying message content, and carefully considering the use of keywords that may trigger filters.
Monitor Deliverability Metrics: Use carrier analytics and third-party monitoring services to continuously track message failure rates, engagement metrics, and overall performance. Investigate sudden changes in deliverability and implement remediation measures quickly.
Establish Relationships with Carrier Compliance Teams: Many carriers offer resources and guidance for businesses attempting to maintain compliance. Building relationships can provide valuable insights about policy requirements and help resolve issues that arise.
Invest in Professional Expertise: If compliance challenges exceed internal capabilities, consider engaging telecommunications consultants, legal specialists, and compliance experts to navigate complex carrier requirements.
The Path Forward: Adaptation and Vigilance
The evolution of carrier policies ultimately stems from a legitimate and important need to protect consumers from fraud, identity theft, and spam. Carriers face genuine pressure from regulators and consumers to clean up their networks and prevent abuse. While these efforts have made it harder for the most brazen fraudsters to operate at scale, they have also created a complex compliance environment that places significant burdens on legitimate businesses.
Organizations must now invest substantially in understanding carrier-specific requirements, maintaining sender reputation, continuously monitoring deliverability metrics, and adapting practices as policies evolve. The ability to reliably reach customers through voice calls and text messages is essential for many businesses’ operations. When that capability is constrained or eliminated due to compliance violations, the impact can be severe.
The most successful businesses will be those that view carrier policy compliance not as a regulatory burden but as an essential component of their operational strategy. By staying informed about policy changes, maintaining best practices, monitoring performance metrics, and being willing to adapt, businesses can effectively leverage voice and messaging channels while respecting the legitimate consumer protection goals that carrier policies uphold. In an increasingly regulated telecommunications environment, policy awareness and adaptive compliance have become essential competencies for any organization that depends on direct customer communication.