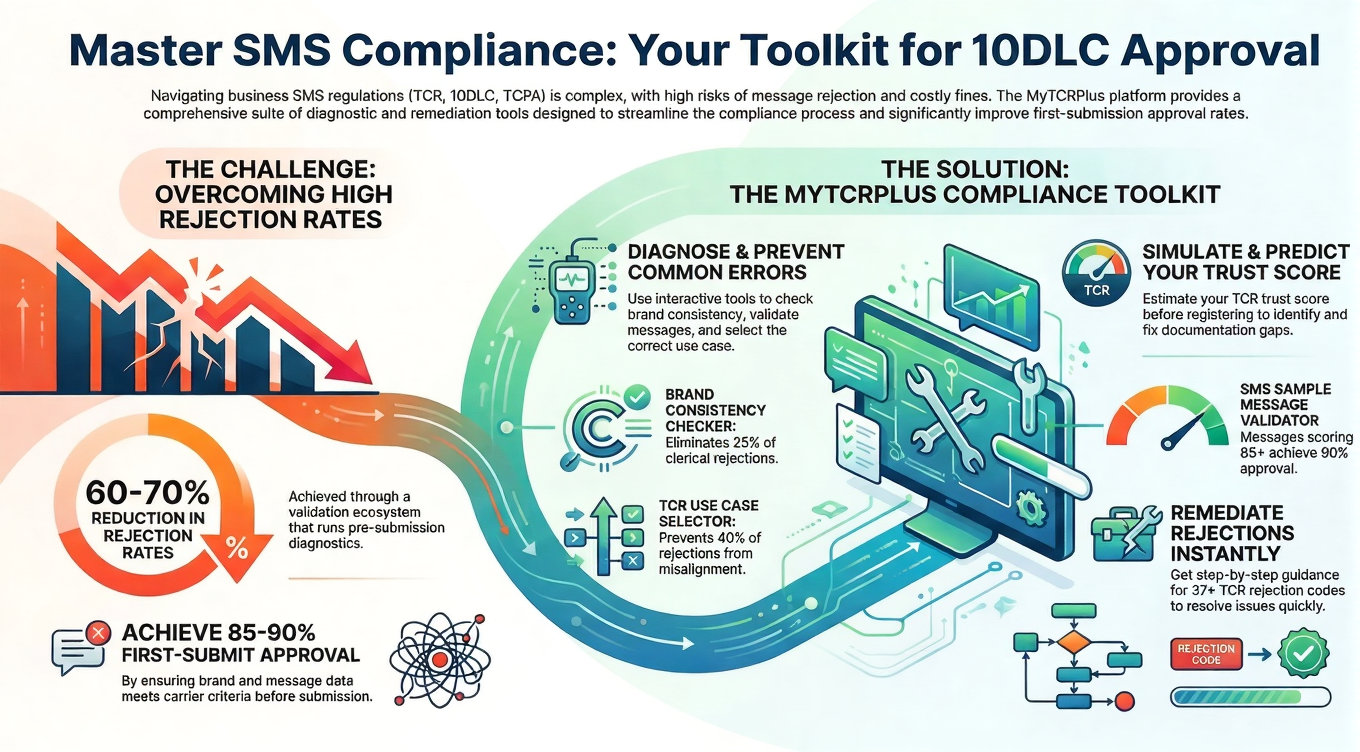
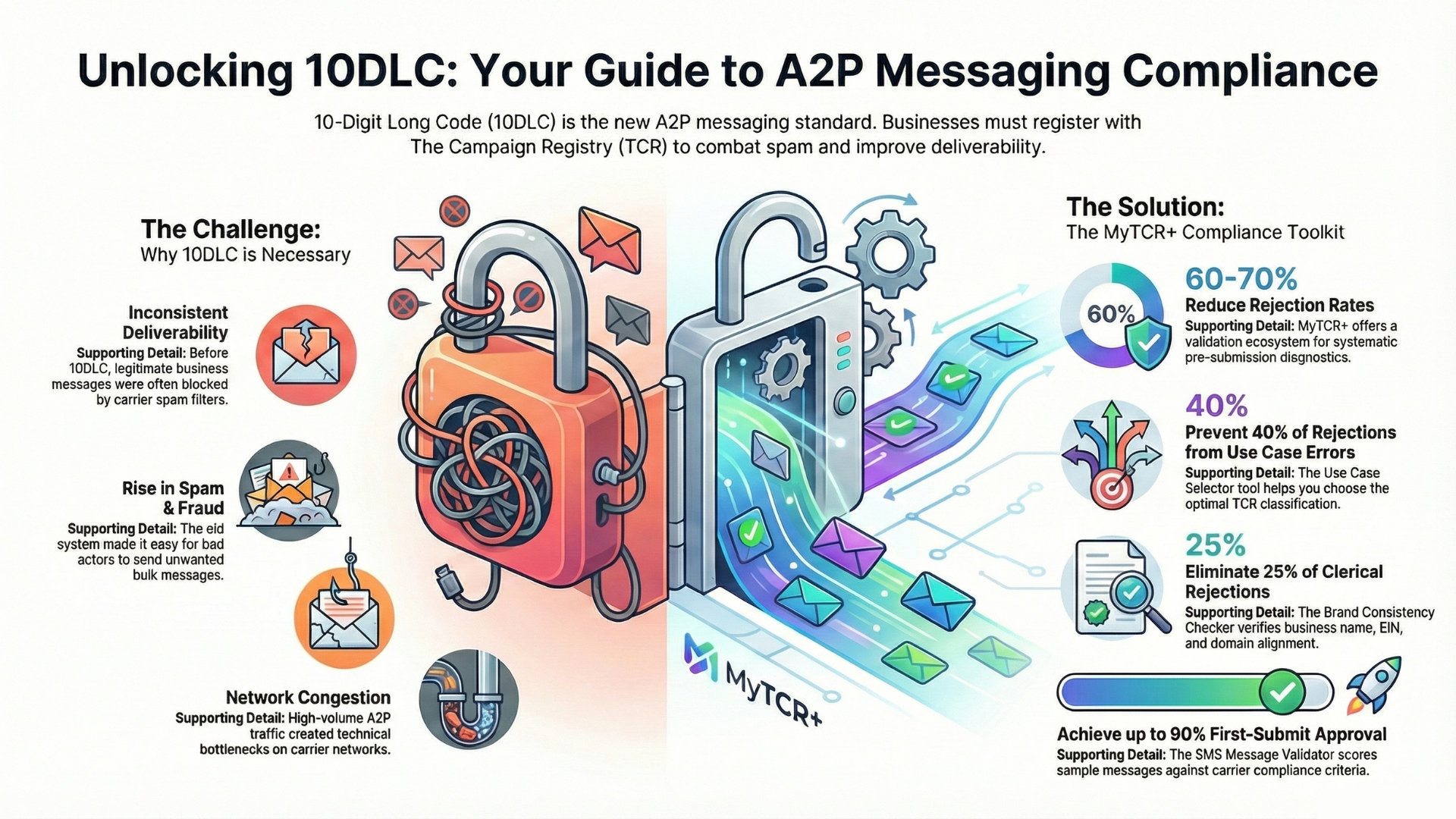
In today’s interconnected digital ecosystem, the sharing of customer data has become both a fundamental business necessity and a significant legal liability. Telecommunications carriers, bound by strict regulatory frameworks and increasingly sophisticated consumer privacy expectations, have intensified their scrutiny of third-party data sharing practices to unprecedented levels. Crafting contractual language that satisfies stringent carrier requirements while maintaining the operational flexibility businesses need to function effectively has emerged as a critical challenge for organizations seeking to establish or maintain carrier partnerships in an environment where data flows are essential but fraught with risk.
The Evolving Landscape of Carrier Data Concerns
The telecommunications industry occupies a unique position in the data ecosystem. Carriers possess extraordinarily sensitive information about their customers, including communication patterns, location data, device identifiers, usage behaviors, payment information, and personal contact details. This information creates immense value for various business purposes but also represents a significant vulnerability if mishandled or improperly shared.
Carriers approach data sharing restrictions with a fundamentally protective stance, viewing themselves as stewards of sensitive customer information rather than merely collectors or processors of it. This stewardship mindset has intensified in recent years as high-profile data breaches, regulatory enforcement actions, and shifting consumer attitudes have made data protection a paramount concern. Their primary concern extends beyond mere regulatory compliance to encompass reputational risk, consumer trust, competitive positioning, and long-term business sustainability.
The consequences of data mishandling have proven severe for carriers who fail to adequately protect customer information. Regulatory penalties under frameworks like the General Data Protection Regulation (GDPR) can reach tens of millions of euros, while Federal Communications Commission (FCC) enforcement actions in the United States have resulted in substantial fines. Beyond financial penalties, carriers face class-action litigation from affected customers, damage to brand reputation that can take years to repair, loss of competitive advantage as privacy-conscious consumers switch to competitors, and increased regulatory scrutiny that constrains future business operations.
When evaluating partnership agreements, carriers examine whether proposed data sharing language demonstrates a genuine commitment to data minimization principles, purpose limitation doctrines, and meaningful consent frameworks that respect customer autonomy. They look for evidence that potential partners understand not just the letter of privacy law but the spirit of responsible data handling. Superficial compliance gestures rarely satisfy experienced carrier legal and privacy teams who have seen countless agreements that promise protection but fail to deliver it in practice.
Building Effective Contractual Foundations Through Precise Definitions
Effective contractual language addressing data sharing begins with explicit, detailed definitions that leave no room for interpretation or creative reinterpretation after execution. Ambiguity in data sharing agreements creates risk for all parties, but particularly for carriers who bear ultimate responsibility for customer data protection in the eyes of regulators and the public.
Rather than broadly referencing “business purposes,” “operational necessities,” or similarly vague concepts, agreements should enumerate specific, legitimate uses for shared data with clarity and precision. This specificity serves dual purposes: it provides carriers with clear boundaries they can defend to regulators, auditors, and potentially customers, while simultaneously establishing unambiguous parameters that downstream partners must observe without room for expansive interpretation.
The most successful agreements identify exact data elements to be shared using technical precision. Instead of referencing “customer information,” effective language specifies “customer mobile telephone numbers and first names only, excluding all other personal identifiers.” Rather than permitting data use for “marketing purposes,” strong agreements detail “one-time SMS message delivery for appointment reminder purposes only, with no retention of numbers after transmission and no use for any promotional or marketing communications.”
These agreements also specify with equal precision the parties authorized to receive information. Generic references to “affiliates” or “service providers” create enormous ambiguity, as corporate structures can be complex and these terms may encompass dozens or hundreds of entities. Better practice identifies specific legal entities by their complete corporate names, jurisdiction of incorporation, and business purpose for receiving the data. This level of detail prevents unauthorized sharing under the umbrella of overly broad contractual language.
Delineating permissible processing activities with granular detail represents another essential component. Strong agreements distinguish between different types of data processing—collection, storage, analysis, transmission, deletion—and specify which activities are permitted under what circumstances. For example, an agreement might permit temporary storage of phone numbers for the sole purpose of message transmission but explicitly prohibit any analysis, profiling, or combination of that data with information from other sources.
The definition section should also address technical concepts with precision appropriate to the technology involved. Terms like “anonymization,” “pseudonymization,” “aggregation,” and “de-identification” carry specific technical meanings, and agreements should define these terms in ways that align with industry standards and regulatory guidance rather than leaving them to potentially divergent interpretations.
Implementing Technical and Organizational Safeguards That Satisfy Carrier Standards
Beyond defining what data will be shared and for what purposes, carriers increasingly focus on how that data will be protected throughout its lifecycle. The incorporation of robust technical and organizational safeguards has evolved from a negotiating point to a fundamental requirement for partnership agreements.
Carriers expect partners to implement industry-standard security measures as a baseline, including encryption both in transit using protocols like TLS 1.3 or higher and at rest using AES-256 or equivalent standards. They require access controls based on least-privilege principles, ensuring that only personnel with legitimate business needs can access specific data elements. Comprehensive audit logging that captures who accessed what data, when, and for what purpose has become standard, providing accountability and enabling investigation of potential incidents.
However, mere promises of security implementation rarely satisfy sophisticated carrier legal teams who have seen too many breaches occur despite contractual security assurances. Instead, contemporary agreements should reference specific frameworks such as SOC 2 Type II compliance, ISO 27001 certification, adherence to NIST Cybersecurity Framework standards, or similar recognized standards. This approach transforms abstract security commitments into verifiable, measurable obligations that can be audited and validated.
Strong agreements go further by requiring periodic security assessments, either through self-certification against defined standards or through third-party audits conducted by qualified assessors. These assessments should occur at regular intervals—commonly annually or biannually—with results provided to the carrier to demonstrate ongoing compliance. The agreement should specify what happens if assessments reveal deficiencies, typically requiring remediation within defined timeframes and potentially granting the carrier suspension rights if critical vulnerabilities remain unaddressed.
Incident response provisions have become equally important. Carriers need assurance that partners will detect, contain, and disclose data security incidents promptly. Effective agreements establish clear notification timelines—often requiring notification within 24 or 48 hours of incident discovery—and specify what information must be provided, including the nature of the incident, the data potentially affected, the number of individuals impacted, remediation steps taken, and ongoing investigation status.
Organizational safeguards complement technical measures. These include mandatory privacy and security training for employees with data access, background checks for personnel handling sensitive information, clear policies and procedures governing data handling, designation of specific data protection officers or contacts, and regular compliance audits. Documentation of these organizational measures provides carriers with evidence of a comprehensive data protection program rather than merely technical controls.
Addressing Temporal Dimensions Through Data Retention and Deletion Requirements
The temporal dimension of data sharing presents another area requiring careful contractual attention that many organizations overlook until carriers raise concerns. Unlike physical goods that naturally depreciate or disappear, digital data persists indefinitely unless actively deleted, creating ongoing exposure that accumulates over time.
Carriers increasingly insist on provisions that mandate data deletion or anonymization once the original purpose for collection has been fulfilled. Open-ended data retention creates ongoing liability exposure that most carriers find unacceptable, particularly as regulatory frameworks increasingly emphasize data minimization and storage limitation principles. The longer data persists, the more opportunities exist for it to be breached, misused, or become subject to regulatory or legal process.
Successful agreements establish clear retention schedules aligned with legitimate business needs while incorporating mechanisms for periodic review and data purging. For example, an agreement for appointment reminder services might specify that phone numbers must be deleted within 48 hours after the scheduled appointment time or immediately upon message delivery, whichever occurs first. A customer service interaction record might be retained for 90 days to enable quality assurance review, then automatically anonymized or deleted.
These retention provisions should address different categories of data separately, recognizing that different types of information have different legitimate retention needs. Transactional records required for accounting or regulatory purposes may require longer retention than communications data used solely for operational purposes. Aggregated or anonymized data may be retained longer than personally identifiable information, provided the anonymization process meets technical standards that prevent re-identification.
Verification mechanisms give these retention commitments teeth. Strong agreements require partners to implement automated deletion processes rather than relying on manual procedures that may be overlooked. They may require certification of deletion, particularly for large data sets, or grant carriers the right to audit data stores to verify that retention limits are being observed.
The agreement should also address what happens to data upon contract termination. Rather than allowing data to persist indefinitely after the business relationship ends, effective provisions require deletion of all shared data within a specified timeframe after termination, often 30 to 90 days, with certification of deletion provided to the carrier.
Managing Downstream Liability Through Comprehensive Subprocessor Provisions
Perhaps most critically, modern carrier agreements must address the cascading nature of data sharing through comprehensive downstream liability provisions. The reality of contemporary business operations is that data rarely remains with a single entity. Primary partners routinely engage subcontractors, service providers, cloud hosting companies, analytics firms, and other third parties who may access or process shared data in various ways.
When a primary partner shares data with subcontractors or service providers, carriers remain exposed to the data handling practices of entities with whom they have no direct relationship, contractual privity, or oversight mechanisms. A carrier’s customer data might pass through a chain of five or six entities, each introducing potential vulnerabilities, compliance gaps, or security weaknesses. A breach or misuse by any entity in this chain creates liability and reputational damage for the carrier, making downstream data flow one of the highest-risk aspects of partnership agreements.
Satisfactory contractual language imposes comprehensive flow-down requirements, ensuring that every entity in the data chain accepts equivalent obligations to those binding the primary partner. This includes provisions mandating that partners obtain written carrier approval before engaging additional subprocessors, requiring detailed information about the subprocessor’s identity, business purpose, data access scope, and security capabilities. Carriers increasingly maintain approved vendor lists and require partners to select subprocessors only from pre-vetted entities.
The agreement should require that any subprocessors execute written agreements containing substantially similar protections to those in the primary agreement. Simply requiring “appropriate” subprocessor agreements creates ambiguity; better practice requires that subprocessor agreements contain specific provisions addressing encryption standards, access controls, audit rights, data retention limits, incident notification requirements, and deletion obligations that mirror the primary agreement.
Liability allocation provisions establish that the primary partner remains fully liable to the carrier for subprocessor actions. Even though the carrier has no direct relationship with the subprocessor, the primary partner cannot insulate itself from liability by claiming a subprocessor acted independently. This creates powerful incentives for primary partners to carefully vet and monitor their subprocessors.
Audit rights should extend to subprocessors, either through direct carrier audit rights or through requirements that the primary partner conduct regular subprocessor audits and provide results to the carrier. These provisions enable verification that downstream entities actually implement the protections contractually required rather than simply promising to do so.
Termination rights provide carriers with remedies when problematic subprocessors are involved. If a carrier determines that a particular subprocessor presents unacceptable risk, the agreement should grant the carrier the right to require replacement of that subprocessor within a reasonable timeframe or, failing that, to terminate the primary agreement without penalty.
Building Flexibility for Evolving Regulatory Requirements
The regulatory landscape surrounding data privacy and protection continues to evolve at an accelerating pace, with frameworks like the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA) and its successor the California Privacy Rights Act (CPRA), and emerging state-level privacy laws in Virginia, Colorado, Connecticut, Utah, and numerous other jurisdictions creating an increasingly complex compliance environment. Additional sector-specific regulations, international frameworks, and carrier-specific requirements add further layers of obligation.
This regulatory evolution creates a challenge for contractual relationships that may last for years. Agreements drafted to meet current requirements may become inadequate as new laws take effect, existing regulations are amended, or regulatory interpretations evolve. Constant renegotiation of partnership agreements in response to regulatory changes is operationally burdensome and may leave gaps during negotiation periods.
Forward-thinking agreements incorporate flexibility mechanisms that automatically adjust obligations as legal requirements change, preventing the need for constant renegotiation while assuring carriers that their exposure remains contained regardless of regulatory developments. These mechanisms take several forms.
Automatic incorporation provisions establish that the agreement will be interpreted to require compliance with all applicable privacy and data protection laws, regulations, and industry standards, regardless of whether specifically enumerated in the agreement. As new laws take effect or existing requirements change, obligations automatically adjust without requiring amendment. These provisions typically include language specifying that in the event of conflict between explicit contractual terms and applicable law, the more protective standard applies.
Regulatory change cooperation clauses commit both parties to work together in good faith to address new regulatory requirements, implementing necessary process changes, technical measures, or contractual amendments within reasonable timeframes. These clauses might establish procedures for identifying applicable new regulations, assessing their impact on the partnership, proposing compliance measures, and implementing necessary changes.
Some agreements establish periodic review mechanisms, requiring parties to meet annually or semi-annually to assess whether the agreement remains adequate in light of regulatory evolution, industry best practices, and emerging threats. These reviews provide structured opportunities to address emerging concerns before they become acute problems.
Suspension or termination rights protect both parties if regulatory changes make the relationship untenable. If new regulations make the contemplated data sharing unlawful or impose requirements one party cannot meet, the agreement should provide off-ramps that allow orderly termination without breach penalties rather than forcing parties into potentially illegal arrangements.
Balancing Carrier Requirements with Operational Reality
While carriers rightfully demand robust protections for customer data, agreements must remain practically executable for partner organizations. Contractual language that imposes impossible technical requirements, demands instantaneous compliance with complex obligations, or creates liability exposure far exceeding the economic value of the partnership will ultimately prove unworkable.
Successful agreements balance carrier protection needs with partner operational capabilities. This balance comes through several approaches. Requirements should be challenging but achievable given industry-standard capabilities and reasonable investment. For example, requiring encryption is appropriate; requiring custom-developed cryptographic algorithms that exceed government standards may be unrealistic for most partners.
Implementation timelines should acknowledge the complexity of technical and organizational changes. While some security measures can be implemented quickly, others require significant development work, testing, and deployment. Agreements that provide reasonable transition periods for implementing new requirements—often 60 to 90 days for significant technical changes—enable compliance while recognizing operational reality.
Proportionality considerations ensure that protection measures align with the sensitivity and volume of data being shared. The same stringent requirements appropriate for sharing extensive personal information about millions of customers may be excessive for a partner that receives only minimal data about a small customer subset for a limited purpose. Carriers increasingly recognize that flexible, risk-based approaches create better outcomes than one-size-fits-all requirements.
Economic allocation of liability should reflect the relative benefits and risks borne by each party. While carriers need protection, liability caps, insurance requirements, and indemnification provisions should be proportional to the partnership’s economic value and the partner’s realistic ability to absorb potential losses.
The Strategic Importance of Getting Data Sharing Language Right
The stakes surrounding data sharing provisions in carrier agreements extend well beyond the specific contractual relationship. How organizations approach these provisions signals their broader commitment to data protection, influences their reputation in the market, affects their ability to secure additional partnerships, and shapes their exposure to regulatory risk.
Companies that develop reputations for taking data protection seriously and negotiating thoughtful, comprehensive data sharing provisions find carriers more willing to engage with them. Those with track records of data incidents, reluctant compliance, or attempts to water down protective provisions face increasing difficulty establishing carrier partnerships as carriers share information about problematic partners within the industry.
From a carrier perspective, the quality of data sharing provisions directly impacts their regulatory posture, their customer relationships, their competitive positioning as privacy-conscious service providers, and their long-term business sustainability. Carriers that consistently demand and enforce strong data protection provisions demonstrate to regulators, customers, and stakeholders that they take their stewardship responsibilities seriously.
Conclusion: Embracing Data Protection as Competitive Advantage
Ultimately, contractual language that satisfies carriers while enabling functional business partnerships must balance specificity with practicality, demonstrating both technical competence and genuine respect for privacy principles that extend beyond mere legal compliance. The most successful organizations view data protection not as a burden or obstacle but as a competitive differentiator and source of sustainable advantage.
As privacy expectations continue rising and regulatory frameworks grow more sophisticated, organizations that establish themselves as trustworthy data handlers will find opportunities expanding while those that resist protection measures face increasing obstacles. The companies that thrive in the evolving data ecosystem will be those that embrace comprehensive data protection frameworks, implement robust technical and organizational safeguards, negotiate transparent and enforceable contractual provisions, and demonstrate consistent commitment to responsible data stewardship.
Navigating third-party data sharing restrictions in carrier agreements requires legal expertise, technical understanding, operational pragmatism, and strategic vision. By approaching these agreements thoughtfully and investing in the capabilities necessary to meet legitimate carrier requirements, organizations can build partnerships that create value while respecting the privacy rights of the customers whose data makes those partnerships possible. In an era where data is both essential and sensitive, getting these agreements right isn’t just good compliance—it’s good business.